Title
Create new category
Edit page index title
Edit category
Edit link
Authentication & Access Tokens
Introduction
Effective token management is critical for secure and efficient API interactions. Passport's API uses an OAuth2 authentication model, ensuring that you can securely authenticate and authorize API requests. This guide provides a structured overview of how to generate, manage, and revoke access tokens.
Bearer Authentication
Bearer authentication (also known as token authentication) is an HTTP authentication scheme that uses security tokens: specifically, bearer tokens. The idea is simple: if you have the token, you're granted access. That’s why it’s called “bearer” the one who bears the token gets access.
Bearer tokens are typically long, random strings generated by the server after a successful login or authorization request. Once you have a token, you must include it in the Authorization header when making requests to protected endpoints:
Authorization: Bearer <token>Authentication Flow
- Register as an Entity: You must register on the Passport platform.
- Obtain API Keys: After completing your registration, you can easily locate your Client ID (API Key) and Client Secret (API Secret) within the dashboard. Navigate to Platform > API Keys.
- Generate an Access Token: Use these keys to request an access token, which grants system-wide API access.
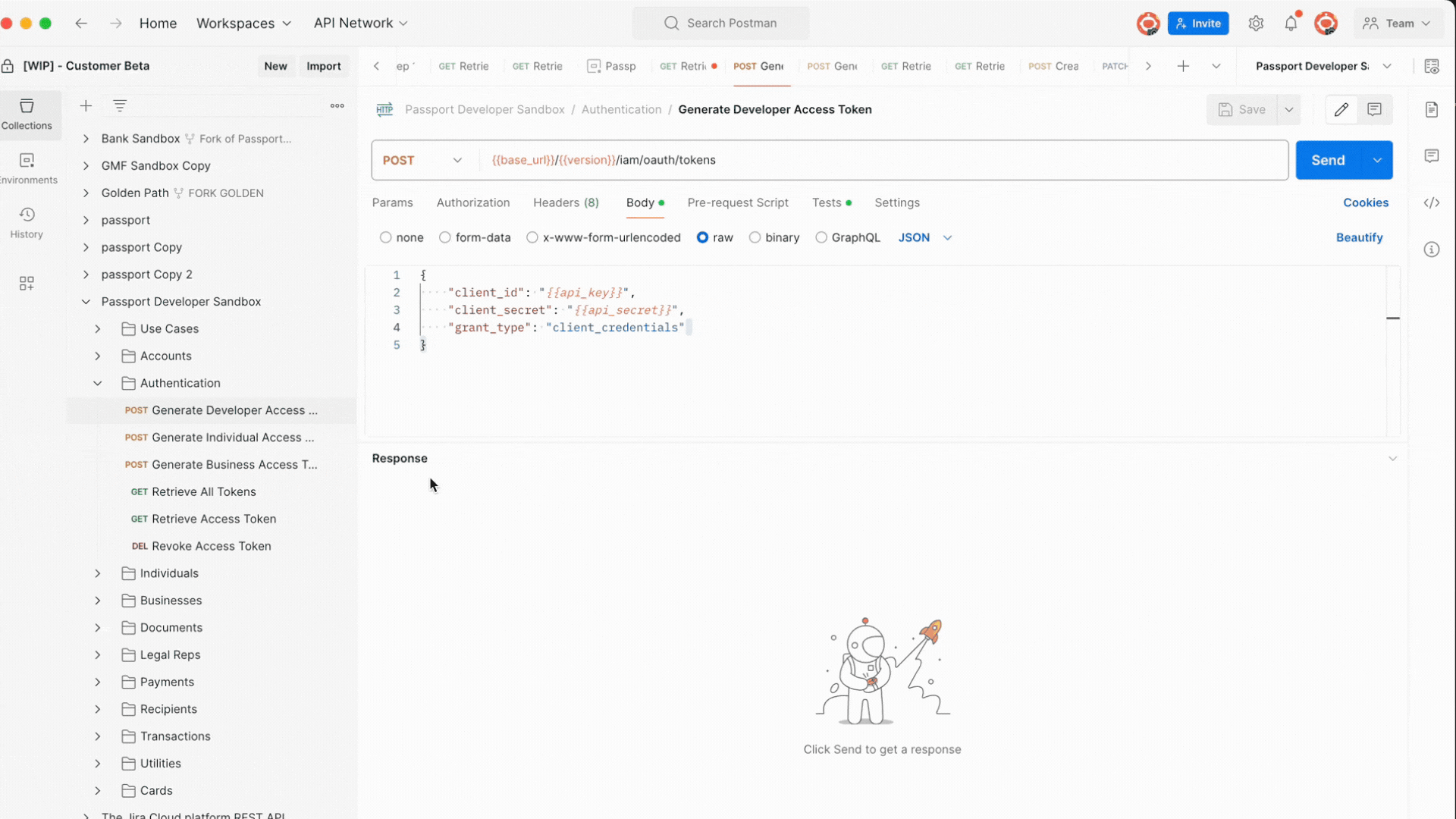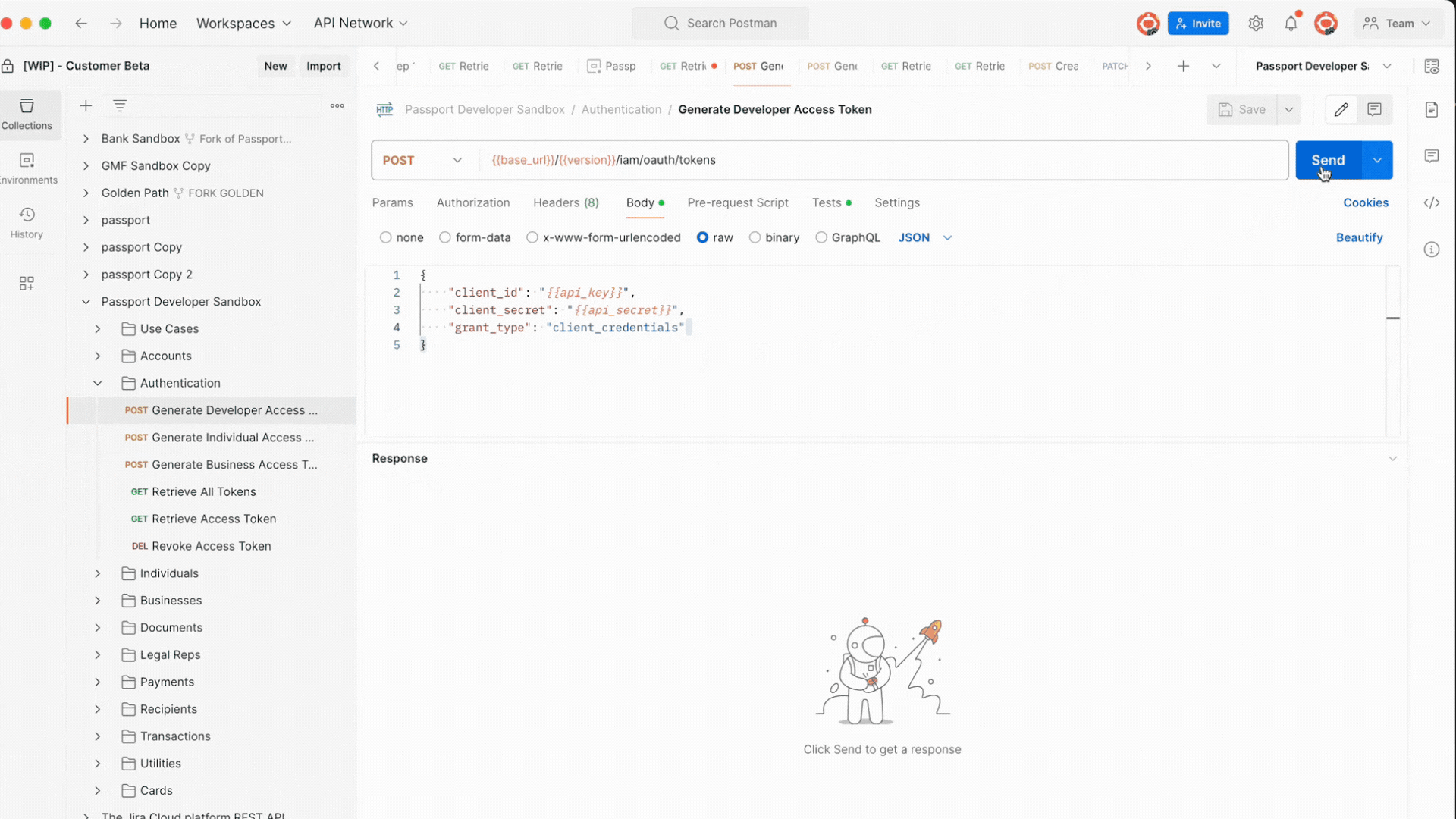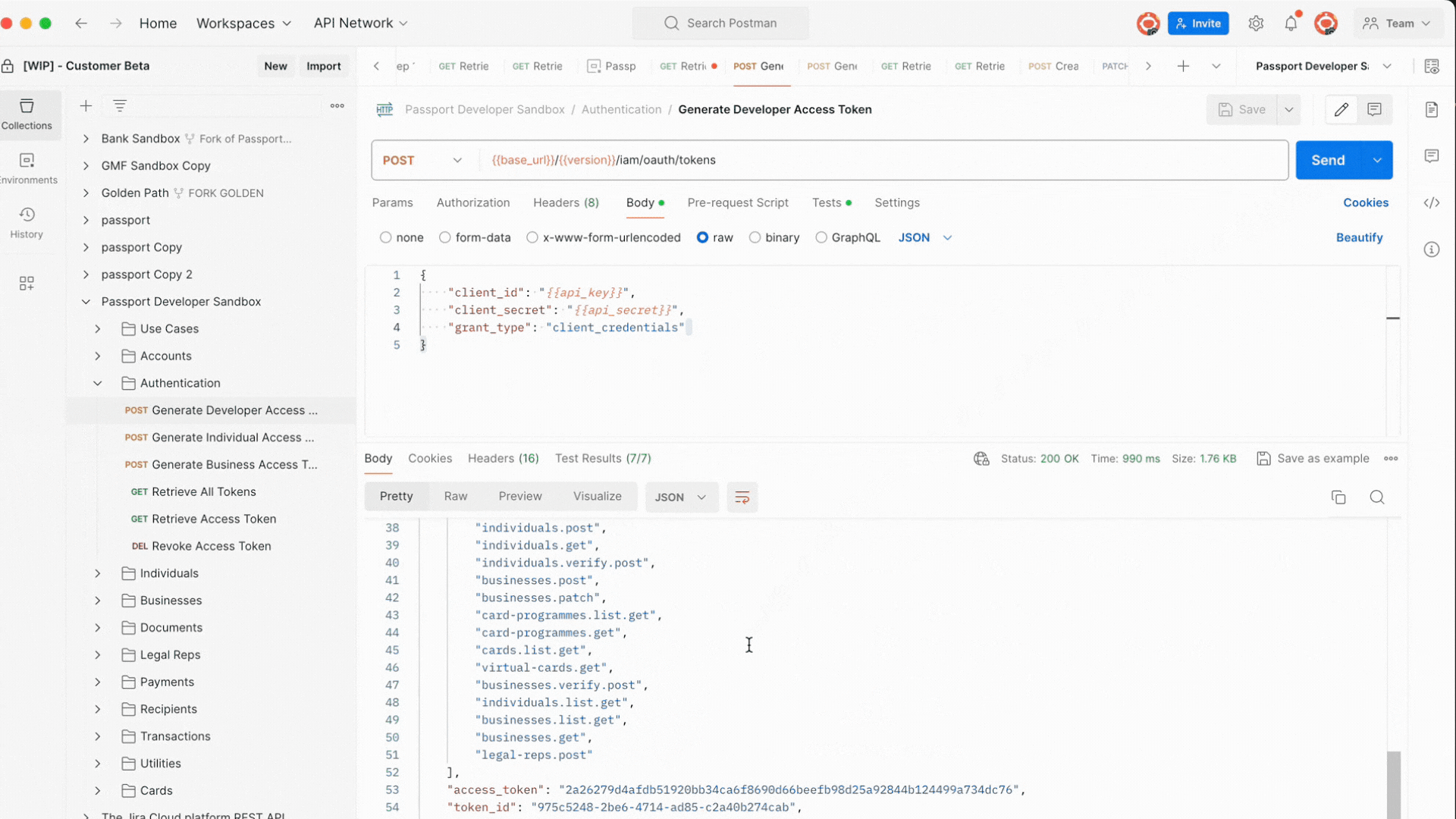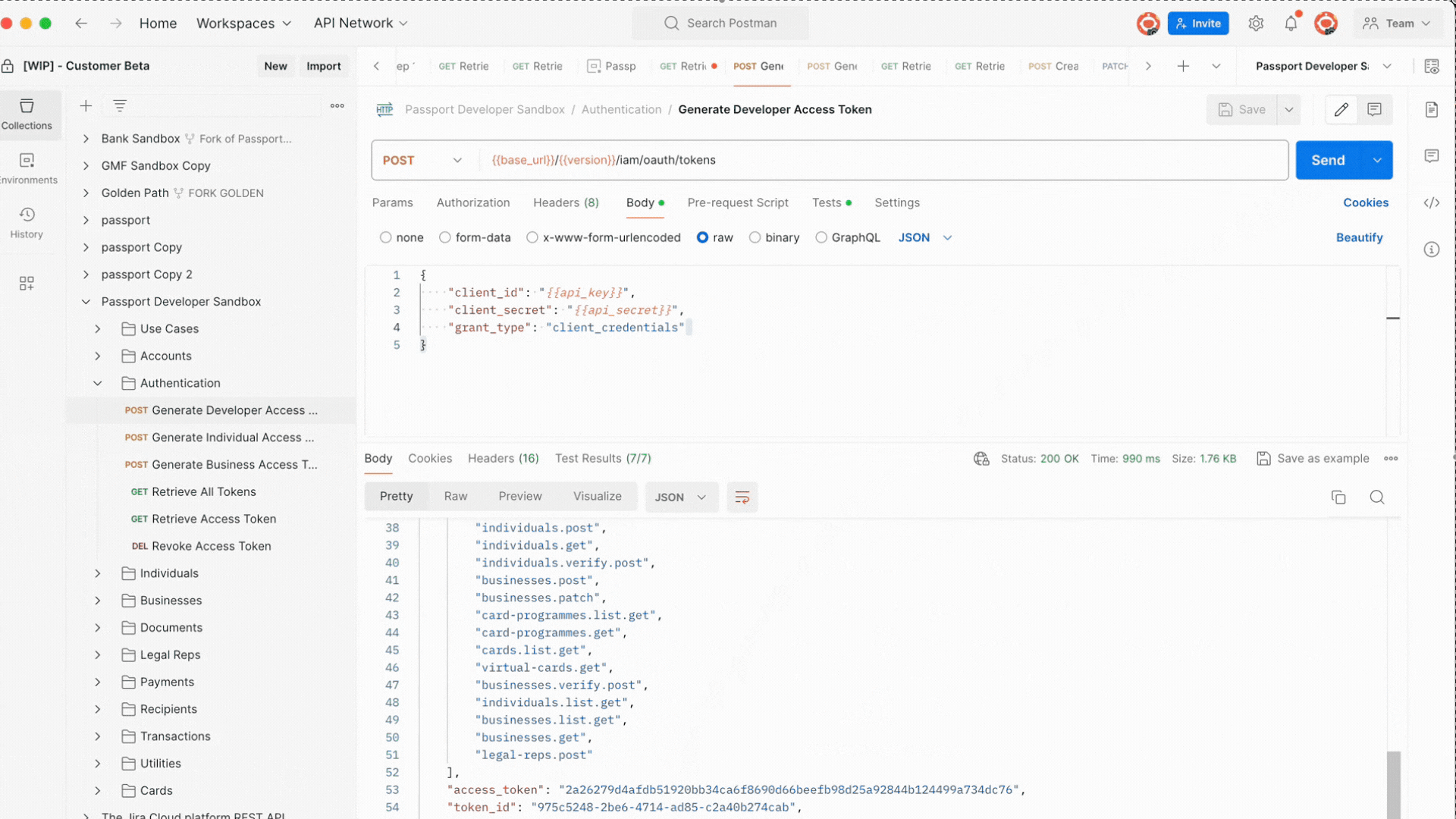
Access Tokens are valid for a duration of 86,400 seconds, which is equivalent to 24 hours. When an access token is generated, you can check its validity by referring to the expires_in parameter.
API Endpoints for Token Management
Generate a Access Token
| Definition | Description |
|---|---|
| Endpoint | https://api.paas.sandbox.co.passportfintech.com/v1/iam/oauth/tokens |
| Method | POST |
| Headers | Accept-Language, Content-Length, Content-Type: application/json |
| Authentication | Client Credentials (API Key and API Secret) |
Request Body Parameters
| Parameter | Type | Description |
|---|---|---|
| client_id | String | Your API Key (Client ID) issued during registration. |
| client_secret | String | Your API Secret (Client Secret) required for authentication. |
| grant_type | String | Must be set to client_credentials to generate a token. |
Example of Request
Access Token Creation
Example of Response
The expected HTTP response body is 200 OK with the follow response body:
Best Practices for Token Management
- Use short-lived tokens: Renew tokens periodically to enhance security.
- Store credentials securely: Never expose API keys or tokens in client-side code.
- Rotate API keys periodically: Regularly update keys to prevent unauthorized access.
Next Steps
Now that you understand how to generate and manage access tokens in Passport, you can proceed with:
- Integrating your credentials into Postman or your development environment.
- Using the generated token to authenticate calls to the platform's various endpoints.
- Exploring the available flows in our Postman collection and detailed endpoint documentation.